Is Multi-Factor Authentication (MFA) Enough to Secure Your Online Accounts?

What is Multi-Factor Authentication (MFA)?
The integrity of your online accounts is more important than ever, and to protect our digital lives, multi-factor authentication has become the gold standard for securing our information, but is it foolproof?
Most people have encountered multi-factor authentication in their lives, whether it’s for a company email, a Netflix account, or online banking. MFA is used in a wide range of applications, from securing personal email accounts to protecting sensitive corporate data. It’s employed by banks, social media platforms, and countless other organizations to add an extra layer of security to their systems. While many of us associate MFA with simple text codes, its applications are far more diverse. At its core, MFA relies on three fundamental principles:
- Knowledge Factor: A secret piece of information, such as a password or PIN.
- Possession Factor: A physical object, like a smartphone or security token.
- Inherence Factor: A unique biological characteristic, such as a fingerprint or facial recognition.
Multi-Factor Authentication (MFA) has become a common security measure, with various methods to implement it. Popular options include:
- Time-Based One-Time Password (TOTP) apps: Such as Microsoft Authenticator or Google Authenticator, generating unique codes for each login attempt.
- SMS or Email Verification: Receiving one-time codes via text message or email.
- Hardware Tokens: Using physical security keys like USB or FIDO devices.
- Biometric Authentication: Employing fingerprint or facial recognition for verification.
While MFA significantly enhances security, it’s not infallible. Cybercriminals can still exploit vulnerabilities in MFA systems, highlighting the need for ongoing vigilance and robust security practices.
The Limitations of MFA: Understanding the Risks
Cybercriminals are constantly evolving their tactics to bypass MFA. One common method is phishing. You might receive a seemingly legitimate email, perhaps a OneDrive invite with the Microsoft logo, that contains a malicious link. Clicking on this link redirects you to a fake login page designed to steal your credentials, including your MFA token. Once they have this information, they can easily bypass MFA and gain unauthorized access to your account.
Token Theft Explained: How Hackers Bypass MFA
Let’s walk through a real-world scenario of MFA token theft, step-by-step.
Step One: The victim receives a phishing email and clicks the link within the email.
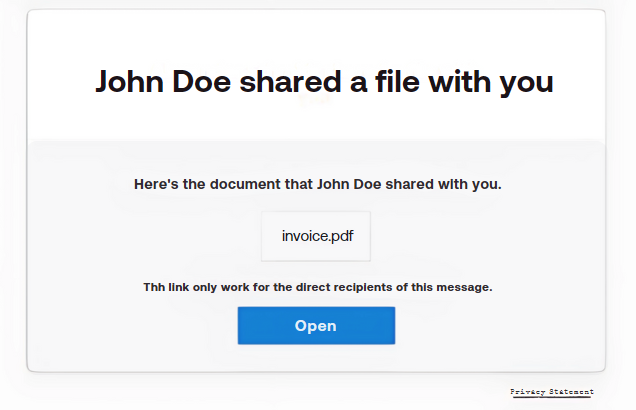
Step Two: The victim clicks the link to open the document and is prompted to enter their username/password.
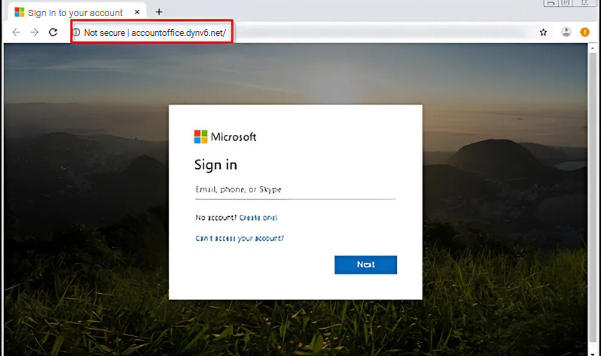
Step Three: The victim enters their MFA code or responds to a push notification on their device.

At this point, the victim has just handed the keys to their digital kingdom to the attacker. Armed with both the password and MFA code, the hacker can now freely access the account. This could lead to a range of malicious activities, from sending spam emails to launching more sophisticated attacks.
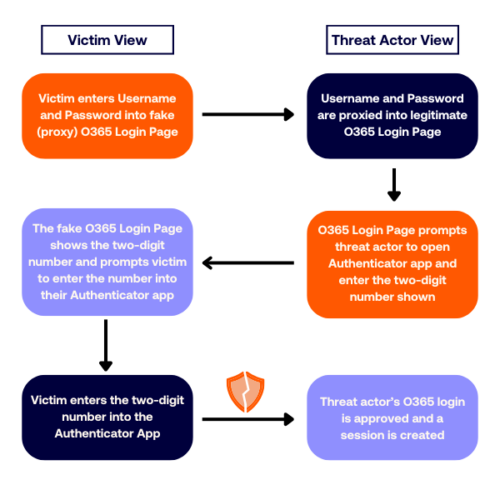
While phishing is one of the most common ways attackers bypass MFA, it’s just one of many methods threat actors use to circumvent security measures. For example, when we rely on SMS for MFA codes, we often assume our phone numbers are secure.
However, attackers can perform a “SIM swap” by using social engineering to deceive mobile carriers. This allows them to transfer the victim’s phone number to a SIM card they control, enabling them to intercept the MFA codes sent via text.
Another common but weak MFA configuration is email-based authentication. The problem with email-based MFA is that if an attacker already has access to the victim’s email account, perhaps through password reuse or phishing, they can easily access the MFA codes sent there. Both SMS- and email-based MFA are vulnerable and should be avoided in favor of more robust authentication methods. It’s crucial to move away from these weaker methods and adopt more secure, complex MFA controls.
Strengthening Your Security Posture: Beyond MFA
It’s a well-known fact that human error remains a significant vulnerability in cybersecurity. According to an IBM study, about 95% of security breaches can be attributed to human error. Despite the widespread adoption of multi-factor authentication (MFA), the risk of unauthorized access persists.
Why MFA Isn’t Enough
While MFA is undoubtedly a powerful tool, it’s not a silver bullet. Cybercriminals are constantly evolving their tactics, and relying solely on MFA can leave organizations exposed. To truly bolster security, a multifaceted approach is essential.
Empowering Users and Enforcing Best Practices
User Awareness: Educating end-users about the latest threats and best practices is crucial. By understanding the risks and the importance of strong security habits, users can become the first line of defense.
Restrictive Policies: Implementing strong authentication policies can significantly reduce the risk of unauthorized access. By enforcing stricter requirements, organizations can make it more difficult for attackers to exploit vulnerabilities.
Advanced Security Measures
Risk-Based MFA: This dynamic approach adapts MFA requirements based on real-time risk assessments. By analyzing factors like IP address, location, and device type, organizations can tailor their security measures to each specific login attempt.
Conditional Access Policies: These policies can be used to enforce additional security measures, such as MFA, for high-risk scenarios. For example, if a user is logging in from an unfamiliar location, they may be required to complete an additional verification step.
A Practical Example: Geo-Location
One simple yet effective way to enhance security is by leveraging geo-location. By restricting logins to specific geographic regions, organizations can significantly reduce the risk of unauthorized access. For instance, if your business primarily operates in the United States, you can configure your systems to block login attempts from outside the country. Let’s further explore this example.
How to Implement Geo-Location-Based Conditional Access Policies
Step One: Define the Policy
Imagine you have a company with employees based in the United States. You want to make sure they only access company resources from approved locations, like the office or their homes.
To do this, you create a policy that applies to all employees. Within the scope of this policy, you can specify the target resources. In this case, the target resource is cloud-based applications like Microsoft 365. So, the policy says: “All employees can only use Microsoft 365 from approved locations within the United States. By setting these conditions, you are ensuring that your company’s sensitive data is only accessed from approved locations.”
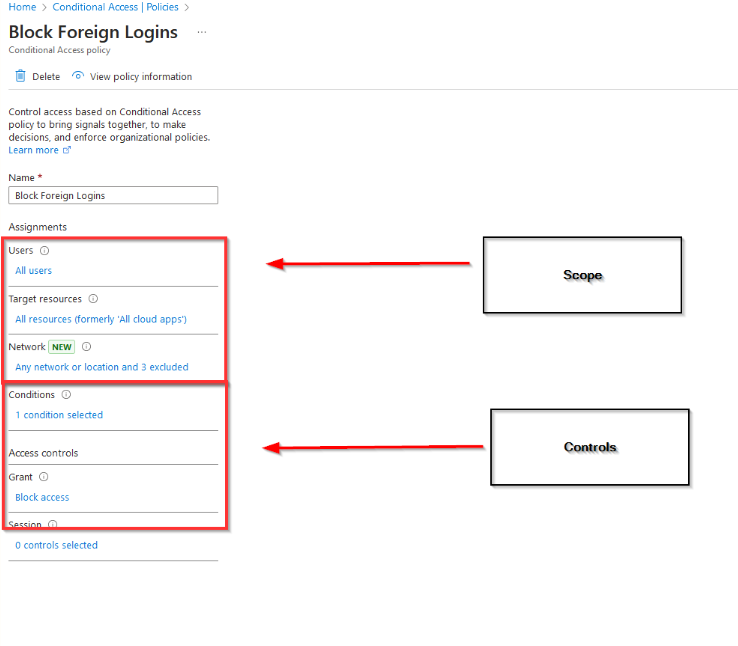
Step Two: Defining Controls
When defining our controls, we are making sure that we are “blocking” as our default condition. This means that any login that occurs outside of the included regions is blocked by default. Additionally, more restrictive conditions can be customized to assess user risk, sign-in risk, insider risk, and device platforms. This is a set of more advanced controls that monitored more in-depth account activity or device activity.
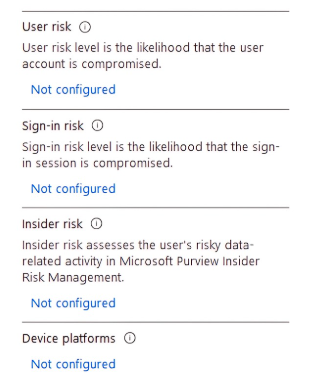
Geo-Location Policies in Action
When considering scenarios where a user falls victim to phishing and their password and MFA token are compromised, additional controls can help prevent threat actors from gaining full access to accounts. A policy like this can be invaluable to an organization, as it helps mitigate the risk of a potential compromise.
In this scenario, Worksighted had implemented a security policy that restricted access to company resources to users located within the United States. In a dangerous misstep, a user fell victim to a phishing attack, directly providing their login credentials and MFA code to cybercriminals via a malicious website.
Upon analysis of the sign-in logs, our team observed multiple failed authentication attempts originating from a Japanese IP address, indicating that the attacker was attempting to exploit the compromised credentials from outside the US.
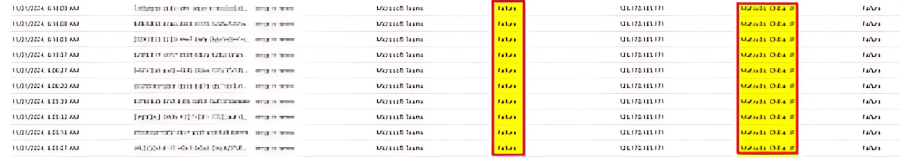
The sign-in logs reveal a clear instance of token theft. The attacker first used stolen credentials to authenticate, then exploited a compromised MFA token.
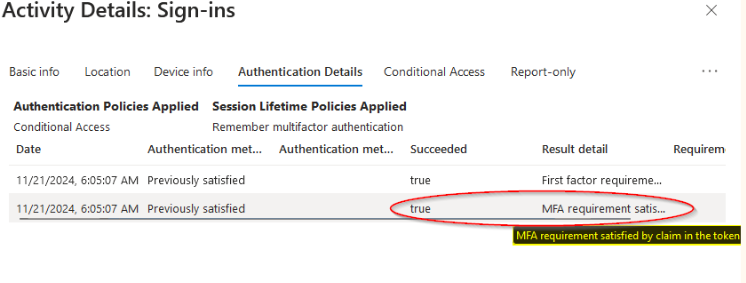
The threat actor had both the password and MFA token, but our policy blocking foreign traffic prevented a successful attack.
![]()
Elevate Your Security Posture Today
MFA is a powerful tool, but it’s not foolproof. To truly protect sensitive data, organizations must adopt a layered security approach that includes user education, robust policies, and advanced security technologies. By prioritizing these elements, organizations can mitigate the risks associated with phishing attacks and other cyber threats.
Want to chat more about your organization’s security needs? We’d love to hear about your specific challenges and how we can help. Reach out to us today, and let’s work together to strengthen your security posture.